Information Theory
pdf | | | Author:Unknown
( Category:
Information Theory
February 1,2023 )
pdf | | | Author:Unknown
( Category:
Information Theory
February 1,2023 )
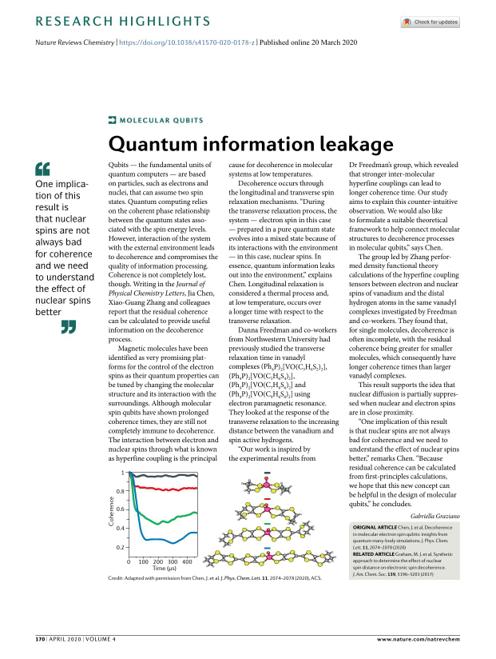
pdf | | 2020-03-27 | Author:Gabriella Graziano
( Category:
Information Theory
January 31,2023 )
pdf |en | | Author: Reza Montasari, Victoria Carpenter, Anthony J. Masys
( Category:
Information Theory
January 6,2023 )
epub |eng | 2022-08-05 | Author:Frank Rubin; [Rubin, Frank]
CC The ciphertext of block N is combined with the ciphertext of block N+1 after enciphering block N+1. For the greatest strength, the chaining operation should be cumulative. First the ...
( Category:
Information Theory
January 1,2023 )
pdf | | 0101-01-01 | Author:Unknown
( Category:
Information Theory
December 19,2022 )
pdf | | | Author:Atmel Corporation
( Category:
Information Theory
October 13,2022 )
mobi, epub, pdf |eng | 2002-08-01 | Author:Williams, Sam [Williams, Sam]
Chapter 8 St. Ignucius The Maui High Performance Computing Center is located in a single-story building in the dusty red hills just above the town of Kihei. Framed by million-dollar ...
( Category:
Software Development
August 2,2020 )
epub |eng | 2012-07-14 | Author:John von Neumann
Modus Operandi of the Memory-Stored Control In this case, since the orders that exercise the entire control are in the memory, a higher degree of flexibility is achieved than in ...
( Category:
Intelligence & Semantics
July 22,2020 )
epub |eng | | Author:Konstantinos Markantonakis & Keith Mayes
10.8.1 Value Added Service Management The situation for value-added service management is less clear than the core SIM functionality and there are a number of different scenarios that need to ...
( Category:
Electronics
July 5,2020 )
epub |eng | 2016-07-11 | Author:Colt McAnlis
Applying delta coding here didn’t produce a less dynamic range, and we still need to encode the entire set with log2(maxValue). But things could become even worse than that. Consider ...
( Category:
Information Theory
July 5,2020 )
epub |eng | 2020-02-11 | Author:Stephenson, Thomas J. [Stephenson, Thomas J.]
Possible advance advice to determine business requirements. The functional requirements, the screen designs and the program sequences for a phase of the project are analyzed, documented, calculated and annulled extensively ...
( Category:
Software Development
July 4,2020 )
epub |eng | | Author:Gerard O’Regan
6.11 Review Questions 1.Describe the main features of the Z specification language. 2.Explain the difference between ℙ1 X, ℙX and F X. 3.Give an example of a set derived from ...
( Category:
Networks
July 3,2020 )
epub |eng | | Author:John F. Dooley
The prisoner has to depend upon the keenness of the person who receives his letter to find out that he has written a message by using the first and last ...
( Category:
Storage & Retrieval
July 1,2020 )
epub, pdf |eng | | Author:Simeon Ball
To construct a generator matrix (g ij) for the Reed–Solomon code, we choose k linearly independent polynomials f 1(X), …, f k(X) of degree at most k − 1 and ...
( Category:
Information Theory
July 1,2020 )
Categories
Popular ebooks
Deep Learning with Python by François Chollet(11960)Algorithms of the Intelligent Web by Haralambos Marmanis;Dmitry Babenko(7884)
Hadoop in Practice by Alex Holmes(5676)
Jquery UI in Action : Master the concepts Of Jquery UI: A Step By Step Approach by ANMOL GOYAL(5529)
Life 3.0: Being Human in the Age of Artificial Intelligence by Tegmark Max(4544)
Functional Programming in JavaScript by Mantyla Dan(3735)
The Age of Surveillance Capitalism by Shoshana Zuboff(3451)
Big Data Analysis with Python by Ivan Marin(3212)
Blockchain Basics by Daniel Drescher(2915)
Test-Driven Development with Java by Alan Mellor(2787)
The Rosie Effect by Graeme Simsion(2734)
WordPress Plugin Development Cookbook by Yannick Lefebvre(2663)
Data Augmentation with Python by Duc Haba(2636)
Hands-On Machine Learning for Algorithmic Trading by Stefan Jansen(2580)
Applied Predictive Modeling by Max Kuhn & Kjell Johnson(2507)
Dawn of the New Everything by Jaron Lanier(2452)
Principles of Data Fabric by Sonia Mezzetta(2448)
The Infinite Retina by Robert Scoble Irena Cronin(2393)
The Art Of Deception by Kevin Mitnick(2319)
Rapid Viz: A New Method for the Rapid Visualization of Ideas by Kurt Hanks & Larry Belliston(2224)